As businesses move further into the world of agile development, they are increasingly creating their own applications. These applications can present a host of vulnerabilities that, if not addressed, could bring down the company. Commercial applications including ERP or CRM systems, databases, office productivity suites, or billing software can act as a host of vulnerabilities. While it’s comforting to think that these proven vendors are laser-focused on preventing software vulnerabilities, vulnerabilities occur nonetheless. In many cases, customers can pay the price.
What Are Software Vulnerabilities?
At a high level, a software vulnerability is a flaw or weakness that can be exploited by bad actors. Those bad actors can use the vulnerability to gain access to an organization’s sensitive data or perform unauthorized actions. No software is immune to vulnerabilities; the key is to find and remediate them as quickly as possible.
The NVD database holds 8,051 vulnerabilities published in Q1 of 2022. This is about a 25 percent increase from the same period the year prior. If these numbers hold, this would mark a slight year-on-year increase since there were around 22,000 published in 2021.
How Do Software Vulnerabilities Happen?
There are many ways that vulnerabilities can get into software, some the fault of the software vendor and some the fault of the user.
On the vendor side, introducing new features can lead to integration errors as well as general bugs and glitches, while upgrades can cause configuration errors along with permission and access vulnerabilities. Any of these errors can lead to security risks, from privilege escalation and security feature bypass to information disclosure, denial of service, spoofing, tampering, or remote code execution.
How Software Vulnerabilities can be prevented?
Precautionary security measures can help businesses prevent the intrusion of hackers into their system that can leverage the existing security flaws of the applications.
- Some of these measures include:
- Assess existing and emerging vulnerabilities
- Run routing software vulnerability tests
- Implementation of a well configured firewall
- Establish a well functioning security monitoring system
- Monitor the performance of the network
- Closely analyze network traffic on the real time
There are many applications in the market one can use to improve the security posture and prevent vulnerabilities in a network. However, the security monitoring process is cost and resource intensive and often unaffordable.
blësk is a cost-effective and complete all in one network monitoring package that will help your organization monitor and prevent software vulnerabilities, which in turn help will help you prevent unauthorized intrusion to your network.
blësk’s Network Security Monitor (NSM) provides a way to continually identify potential vulnerabilities on systems and produces a detailed plan on how to remediate and remove those vulnerabilities from your critical business systems.
The NSM function, allows to automatically scan a subnet of a network based on a custom schedule and it automatically reports the results to the administrator by email in different formats. The NSM module allows to define targets for vulnerability scans, which may be a single IP or range of IP addresses to execute NVT script towards targeted system(s) to test for vulnerabilities and it allows to schedule the frequency of running the test. 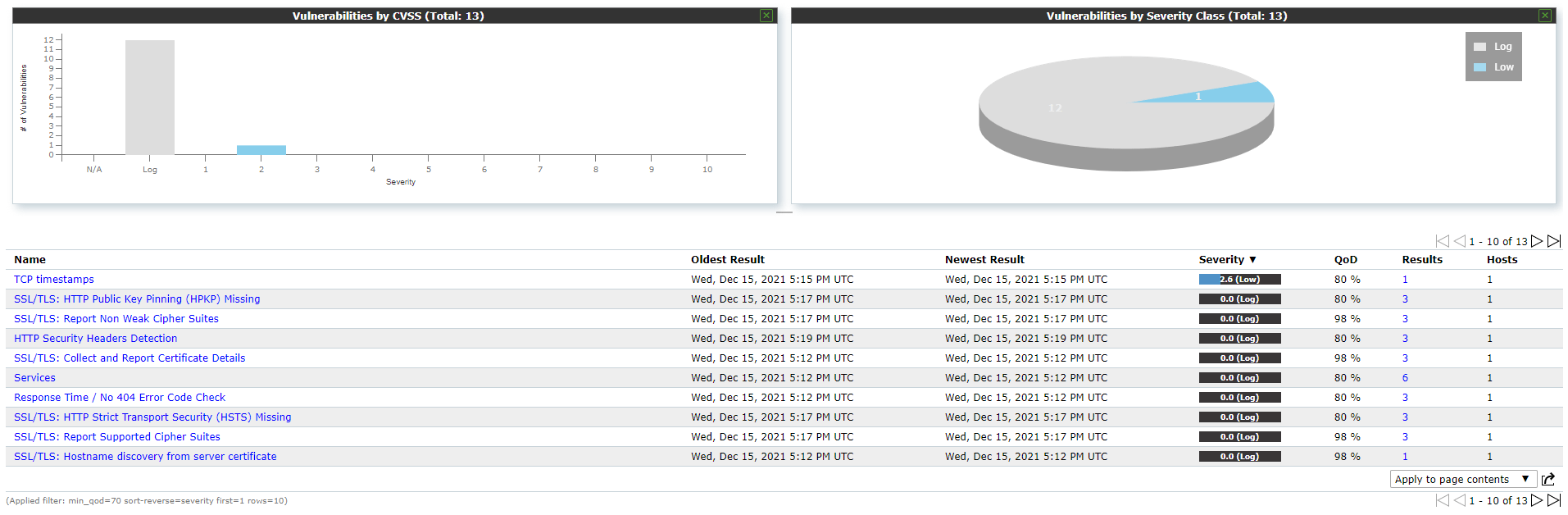
Figure 1: Vulnerability scanning
The Network Security Monitor allows to create infinite custom dashboards for groups of devices for the ease of monitoring devices by device type.
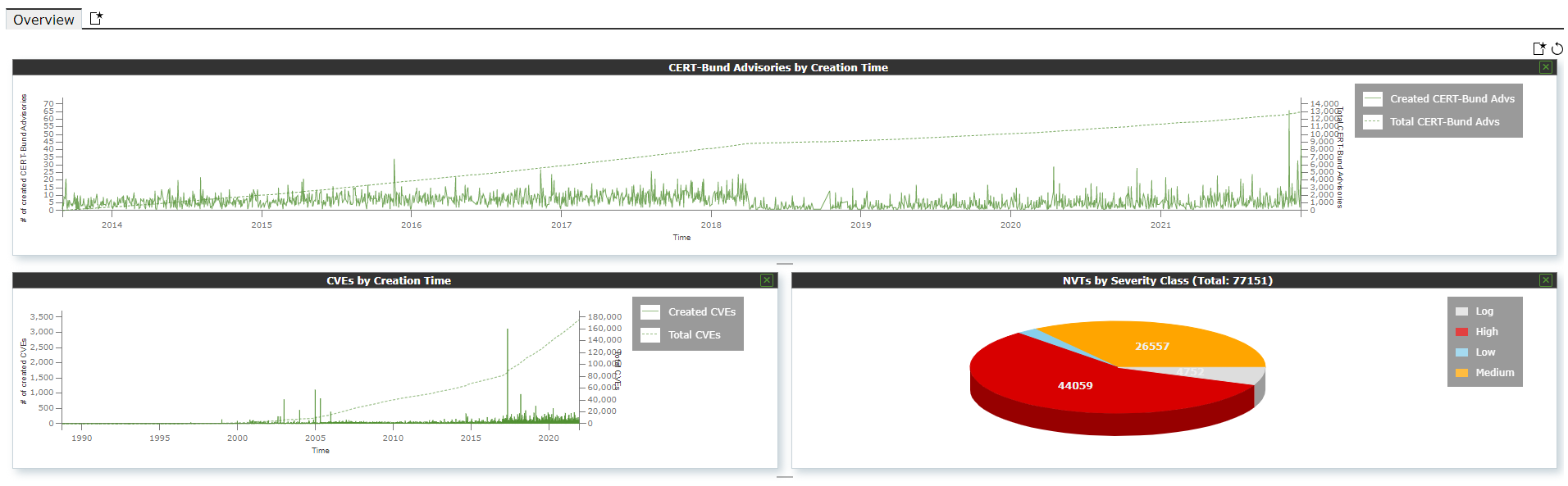
Figure 2: Vulnerability classification
Network Security Monitor (NSM) runs vulnerability tests using the updated vulnerabilities found in the Common Vulnerabilities and Exposures (CVE) reference database as well as CPEs, OVAL, and CERT.
A managed service can be an option for to overcome the challenge of resource limitations
We understand that some organization may don’t have inhouse capacity to facilitate many essential tasks; therefore, blësk offers managed services to the low resourced organizations to monitor their network services.
Download a free trial of blësk on https://www.blesk.ca/essai-gratuit/